
PCI DSS Compliant businesses: How Parallels RAS helps
Introduction
IT security has always been a significant concern for businesses that accept online credit card payments. They hold sensitive information that malicious hackers are after cardholder data and customer information. This is why businesses are legally obliged to build PCI DSS compliant IT infrastructures.
The 4 Levels of Compliance
There are four (4) PCI DSS compliance levels, namely:
- Level 1: Merchants with more than six million transactions credit or debit card transactions annually belong to this level. They are required to undergo a yearly internal audit by an authorized PCI auditor and a quarterly PCI scan by an approved Scanning Vendor (ASV).
- Level 2: Merchants with 1-6 million credit or debit card transactions annually belong to this level. They are required to complete an annual Self-Assessment Questionnaire (SAQ) based on their level and an optional quarterly PCI scan.
- Level 3: Merchants with 20,000 to one million credit or debit card transactions belong to this level. They are required to complete an annual SAQ based on their level and an optional quarterly PCI scan.
- Level 4: Merchants with less than 20,000 credit or debit card transactions belong to this level. They are required to complete an annual SAQ based on their level and an optional quarterly PCI scan.
What Is PCI DSS?
PCI DSS is a security standard developed by the Payment Card Industry (PCI) Security Standards Council. Designed for businesses that do online transactions and hold customers’ payment records, it helps them build and maintain secure IT infrastructure, ensuring the privacy and security of cardholder data.
The set of standards defined in the PCI DSS is the minimum required level of computer systems security that must be in place when processing credit card data. These standards apply to merchants, processors, financial institutions, service providers, and any other entity that stores, processes, or transmits credit card and cardholder information.
What are the 12 requirements for PCI DSS Compliance?
To be PCI DSS-compliant, organizations must meet the following minimum requirements:
- Use firewalls to protect systems: Firewalls are required to prevent unauthorized access to systems from within internal and external networks.
- Replace default passwords and pre-configured system settings: Default passwords and settings in vendor-supplied systems may compromise their security. Make sure to change them to avoid potential security issues.
- Secure stored cardholder data: There are certain data that should never be stored, e.g. the CVV and PIN. If you have to store cardholder data, use encryption, among other methods, to secure them. Document data retention and disposal policies for stored cardholder data.
- Encrypt cardholder data during transmission: Industry-standard encryption protocols must be used when transmitting cardholder data across public networks such as the Internet.
- Use antivirus and other software: Update anti-virus and similar programs installed on your systems.
- Secure your systems: Regularly update your systems with vendor-supplied patches.
- Restrict access to cardholder data: Implement authorization mechanisms to ensure that only those with the need to know have access to critical data.
- Assign unique IDs to systems: All users must have unique IDs. Implement password management and user authentication management mechanisms and use two-factor authentication for remote access.
- Restrict physical access to systems: Only users authorized to do so are able to physically access systems. Secure all media and destroy them when not needed anymore.
- Log all system usage: All systems must have audit trail mechanisms for logging all user activities.
- Test security systems and processes regularly: Systems must be tested on a regular basis to ensure their security. Use intrusion detection and prevention techniques to secure systems.
- Document your security policy: All personnel are required to follow an information security policy that evolves with the threat environment.
Why Businesses Need to Be PCI DSS Compliant
The challenges of building and maintaining PCI DSS compliant networks are many and depend on several factors. For example, the software used network setup and the procedures in place. If organizations that process credit card payments and store cardholder details fail to build PCI DSS compliant networks and computer systems, they risk being fined up to $500,000 per month – or even worse, having their trading license revoked.
This white paper explains how using Parallels® Remote Application Server (RAS) can help organizations build scalable PCI DSS compliant networks and save on costs and administration overheads.
What Is Parallels RAS?
Parallels RAS is server software that enables organizations to build a private, secure cloud from which they can provide vendor-independent virtual desktop and application delivery from a single centralized platform. Parallels RAS extends and optimizes Windows RDSH host pools and supports all major hypervisors from Microsoft, VMware, Citrix, and others.
All published applications and virtual desktops run on servers inside the datacenter. Users can access published applications and desktops using native Parallels RAS Clients or via HTML5-enabled web browsers. Since the user experience is provided via clients, the data and published resources never leave the private cloud, thus ensuring its security.
Apart from cutting down on costs, organizations using Parallels RAS also improve their productivity by being able to quickly deliver applications, desktops, and data to anyone, anywhere.
How Parallels RAS Helps Build PCI DSS Compliant Systems
PCI DSS is based on a set of twelve security requirements. Businesses are inquired to implement these security measures to ensure compliance with the Payment Card Industry Data Security Standard.
Build and Maintain a Secure Network and Systems
Requirement 1: Install and maintain a firewall configuration to protect cardholder data.
PCI DSS compliant networks require that all cardholder data flow across systems and networks – both trusted und untrusted – using secure protocols and network firewalls that allow incoming traffic from allowed devices only.
Parallels RAS simplifies this scenario; it allows businesses to easily control access to the data and published resources both at the gateway level and published resource level. Administrators can specify which devices are authorized to connect to the environment and access data with the policy settings by limiting access based on gateway, MAC address, client type, IP address, user, or group.
Requirement 2: Do not use vendor-supplied defaults for system passwords and other security parameters.
Parallels RAS is integrated with Microsoft Active Directory, through which administrators can easily enable or disable users and set password-complexity requirements. On Parallels RAS, they can also control user access and logon times, as well as integrate the system with third-party authentication servers to enable robust authentication mechanisms such as two-factor authentication.
Protect Cardholder Data
Requirement 3: Protect stored cardholder data.
Parallels RAS provides businesses with a complete toolset to build a secure environment in which they can run software to store cardholder data. All process flows, and cardholder data stay in the data center, which eases being PCI DSS compliant and reduces security costs to protect the data. Parallels RAS also provides a comprehensive client management solution that allows administrators to completely lock down client guests by configuring user policies that transform endpoints into a thin client (kiosk mode).
Requirement 4: Encrypt transmission of cardholder data across open, public networks.
Parallels RAS supports both Secure Socket Layer (SSL) and Transport Layer Security (TLS) protocols to guarantee a secure communications channel between clients and the customer cloud infrastructure.
Administrators can choose between setting the SSL decryption process to be performed on the High Availability Load Balancing (HALB) appliance, which is also used to load balance incoming traffic or tunnel the SSL connections directly to the Secure Client Gateways. In addition, SSL/TLS must be enabled and configured on the Parallels RAS Gateway to allow access from HTML5-enabled web browsers.
Maintain a Vulnerability Management Program
Requirement 5: Protect all systems against malware and regularly update anti-virus software or programs.
When using Parallels RAS, all infrastructure components and data are not stored in the endpoint client device. This allows administrators to install anti-virus and similar protection software in a central location, thus making it very easy to ensure it is kept up to date and working. Running such software in a central location reduces the risks of a data breach. Furthermore, for mobile users, Parallels RAS provides HTML5 access with highly strict access rules.
Requirement 6: Develop and maintain secure systems and applications.
Administrators know very well that applying security patches is a problematic task. Compatibility issues, software crashes, user permissions problems, unsupported hardware, and several other issues are just a few that administrators encounter when applying security patches. There is no way to avoid this; administrators must install the vendor-released security patches to ensure the security of their network and sensitive data.
Parallels RAS has policies allowing administrators to manage desktops assignments and disconnections of company users. For example, once a user logs off, depending on the policies, the user desktop can be shut down, suspended, or rebooted. This, in addition to allowing complete control of desktops assignment, also provides efficient and optimal use of the company resources.
With all business applications running in the enterprise cloud and published through Parallels RAS, security breaches mitigation becomes a more affordable task. Operating systems and applications are centrally updated in a short space of time, and there is much less that needs to be updated. Also, with Parallels RAS, users do not have access to install software; the applications catalog is limited to the software each user can run, and running processes on each VDI user can be centrally managed. Parallels offer the option of verifying access to published applications before making them available to the end-user, ensuring resources are available in the specified path, and compatibility issues do not appear after the product’s or operating system’s patching process.
Implement Strong Access Control Measures
Requirement 7: Restrict access to cardholder data by business need-to-know basis.
To ensure critical information such as cardholder data can only be accessed by authorized personnel, Parallels offers a comprehensive set of policies to determine which clients can run, which publish applications. Policies allow administrators to manage and define client requirements for users on the network who connect to a server in the farm. Based on different criteria, such as client MAC address, client type, or Parallels RAS Gateway, different session settings can be defined for each client connected to the environment.
Requirement 8: Identify and authenticate access to system components.
PCI DSS-compliant solutions must provide a unique identification account to each user who connects to the infrastructure. Parallels RAS is wholly integrated with Microsoft Active Directory, where each user has its unique ID (User Principal Name). Complementarily, the new Windows10 PIN unlock feature is completely integrated with RAS client Single Sign-On.
Parallels RAS can also be integrated with third-party multifactor authentication solutions such as DualShield, Safenet, RADIUS, or Azure Multi-Factor Authentication. Google Authenticator, using the Time-Based One-Time Password (TOTP) algorithm, has also been recently added as an MFA provider. Assigning a unique identification to each user guarantees that each person is traceable for their actions.
Your company-published resources can be restricted from being accessed only through the RAS Infrastructure, thus enhancing your company security and preventing forbidden accesses.
Requirement 9: Restrict physical access to cardholder data.
This is not something that Parallels RAS or any other software can help you. However, since Parallels RAS stores all data centrally, it makes it much easier to restrict physical access to servers where cardholder data is stored.
Regularly Monitor and Test Networks
Requirement 10: Track and monitor all access to network resources and cardholder data.
Tracking end-to-end user activities are critical in detecting, preventing, and minimizing possible unauthorized access to applications or even to stored cardholder data.
Parallels RAS offers complete tracking configuration options for the administrators’ activity (audit log of what administrators are doing and changing in the environment configuration) and logs what is changed in RAS console to avoid, for instance, unauthorized access grants. Apart from the default audit log, several other types of logs can be enabled in the Parallels RAS farm or multi-farms. Log rotation and other settings can be configured on each host, depending on the security requirements.
Additionally, several user monitoring features (such as the monitoring report or the client manager) and custom reports can be used to help administrators keep track of all the accesses, application usages, and events happening on their infrastructure to spot any suspicious behavior immediately.
On top of that, Parallels also has a tool to delete all information about a specific user, easing the General Data Protection Regulation (GDPR) compliance maintenance.
Requirement 11: Regularly test security systems and processes.
This is not related to the network setup, and Parallels RAS cannot help you with this requirement. However, because of the way Parallels works and can be set up, it is effortless for administrators to test the system and processes since everything is centralized in the data center or private cloud.
Maintain an Information Security Policy
Requirement 12: Maintain a policy that addresses information security for all personnel.
Employees working in a cardholder-data environment should be aware of the sensitivity of data and their responsibilities for protecting it. The easier they can access the environment from client devices, the easier for Administrators to avoid security problems. As all Parallels RAS infrastructure components can be in the company data center or private cloud and client-side requirements are minimum, companies can easily document and establish simple user procedures to connect to their critical applications.
Sample Diagrams for PCI DSS Networks
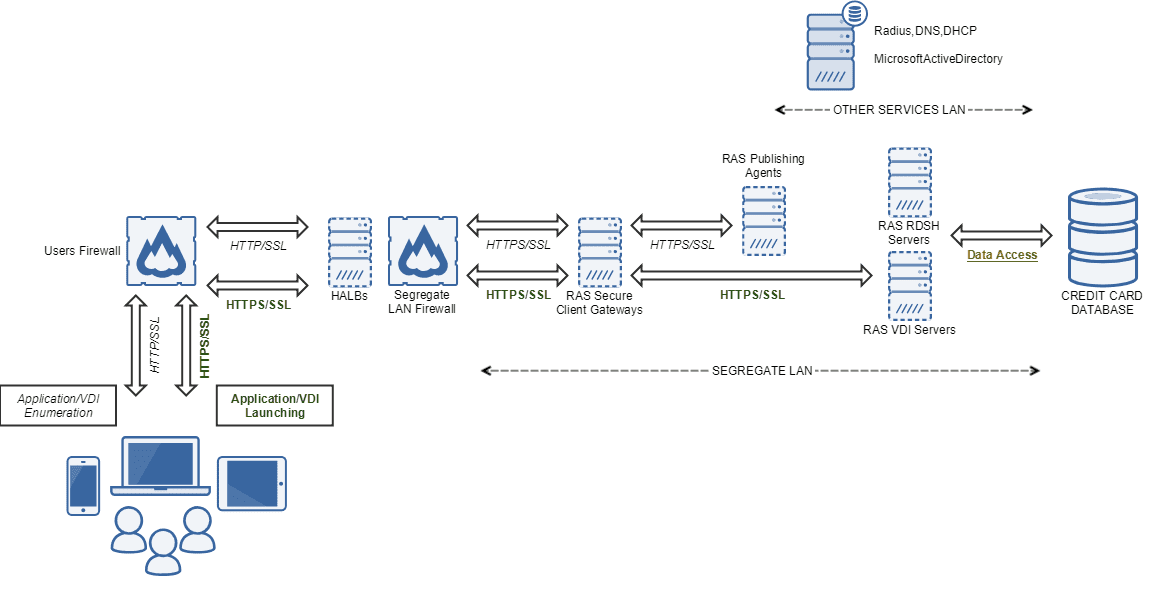
PCI DSS-Compliant Local Network Implementation
The diagram below highlights how Parallels RAS can be implemented in a LAN environment to build a PCI DSS-compliant network. Some of the features that organizations can benefit from when using this scenario are:
- Applications used to access cardholder data are segregated from the LAN
- The cardholder data database is segregated from the LAN
- All applications are only available through a central location: Parallels RAS
- All sensitive data is stored in a central location
- Users access applications and data over an encrypted channel
- Sensitive cardholder data never leaves the private cloud
- Only publishing data is transferred between the user and the private cloud
PCI DSS Compliant Network with Remote Access Implementation
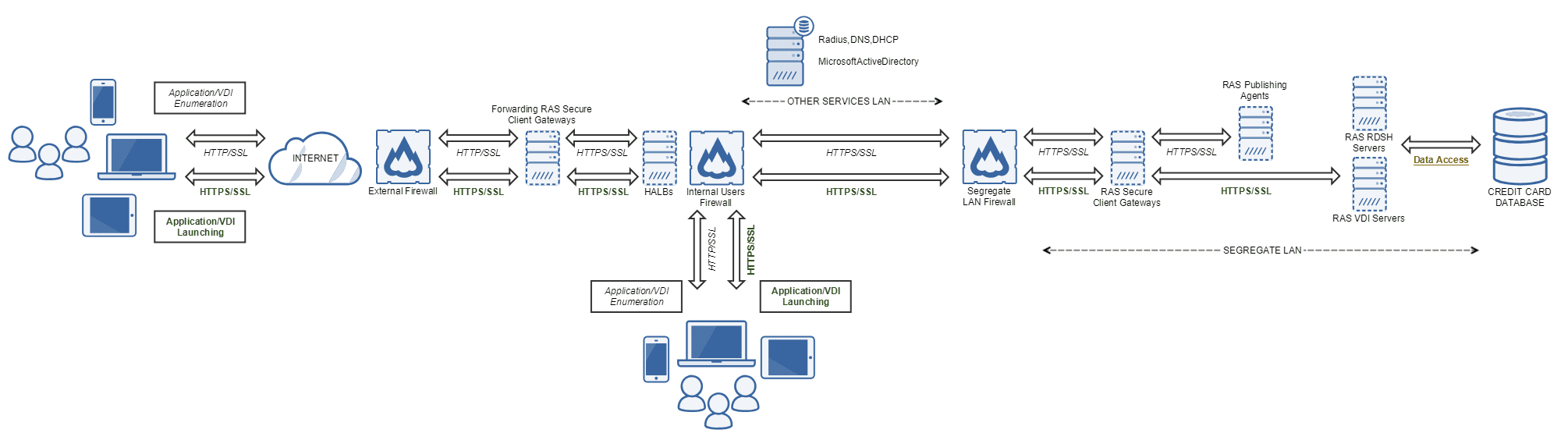
The diagram below highlights how Parallels Remote Application Server can be implemented to build a PCI DSS compliant network and provide access to remote users. These are some of the features organizations can benefit from:
- All of the benefits that apply to the local area network implementation mentioned in the previous
- Remote users can access applications and data by using the RAS Client, which can run on any modern operating system and mobile
- Remote users can access applications and data from a standard HTML5 browser over an HTTPS
- Multiple firewalls allow for segregation of private cloud, local area network, DMZ and corporate network
Other Notable Features that Make Parallels RAS Perfect for PCI DSS Networks
Installation and Setup: Time Investment
All the components required to set up the site are installed through a single MSI file, a very straightforward process for an “all-in-one” solution. The default setup is focused on helping businesses get started very quickly with configured SSL certificates, remote access, and fully enabled HTML5 client support. Furthermore, Parallels RAS offers an all-in-place upgrade for all versions with minimal downtime. When using Parallels, your environment can be upgraded without affecting your users’ productivity.
Flexibility in Deployment (On-Premises, Hybrid, and Cloud)
Parallels RAS supports on-premises, hybrid, and cloud deployments. It is readily available for both Microsoft Azure and Amazon Web Services™ (AWS) Marketplace as a Windows Appliance.
Simple Pricing and Low Licensing Costs
There is only one edition of Parallels RAS, and it includes all the enterprise features such as reporting, load balancing, and high availability. The affordable Parallels RAS licensing model depends only on the number of concurrent users connecting to the environment.
Centralized Configuration Console and Multisite Support
To manage, monitor, and scale up the Parallels RAS farm systems, administrators only use a single central interface, the Parallels RAS Configuration Console. This console also allows system administrators to manage interconnected farms in different physical locations centrally. This gives system administrators in a multisite environment the flexibility to better utilize all available resources because users from one site can access published applications and virtual desktops on another site.
Multiple Administrators and Roles Make Delegation Easier
Delegating administrative tasks has never been easier. Administrators can assign different Parallels RAS roles to Active Directory users so that each administrator account can configure and maintain a specific function. For example, an administrator can manage the publishing of applications and other resources for a specific site.
Best-in-Class BYOD Support for a Wider Variety of OSes and Mobile Devices
Parallels RAS client is available for Windows, Mac, and Linux operating systems. It can also be installed on virtually any type of mobile device, such as the popular Android and iOS phones. An HTML5-enabled browser allows users to view and launch remote applications or virtual desktops in a web browser, making Parallels RAS a client-independent solution that’s perfect for bring-your-own-device (BYOD) scenarios.
Easy Partial and Full Recovery Options
Parallels RAS allows Administrators to import or export configuration from the central Parallels RAS Console. If a backup needs to be restored, the process is simple, efficient, and fast, ensuring the least possible downtime.
High Availability
An out-of-the-box installation of Parallels RAS load balances all the incoming connections. Parallels RAS has a built-in and management-free High Availability Load Balancing (HALB). It can distribute load among servers and gateways based on the resources available, dramatically improving the user experience.
A Complete VDI Management Solution
In some scenarios, Administrators may need to provide users with a full desktop instead of just a published application. Parallels RAS offers a complete virtual desktop infrastructure (VDI) solution included with its licensing plan. Furthermore, Parallels RAS supports desktop pool generation from linked clones, which in conjunction with RASprep technology, allows absolute flexibility in the creation of new user desktops. Easy to recycle machines and possible to generate new ones in case some have been infected by malicious software in a short space of time.
Windows Server 2019 Support
All RAS Infrastructure components are compatible with Windows Server 2019. Additionally, Virtual Desktop Infrastructure (VDI) desktops and Remote Desktop Session Host (RDSH) servers can be provisioned, scaled, and maintained on Microsoft Hyper-V 2019.
Session Pre-Launch
With RAS, administrators can enable the session pre-launch feature to reduce application launch time. Using cutting edge Artificial Intelligence (AI) technology, RDP sessions are started automatically just a few minutes before the user starts the applications typically to improve the user experience and reduce waiting times.
VDI solution Scale Computing HC3 Support
Among the complete list of supported hypervisors, such as VMware ESXi and Microsoft Hyper, RAS also supports Scale Computing HC3 support for VDI deployments. Scale Computing HC3 is a new hyper-converged infrastructure that includes computing, storage, virtualization, backup, and disaster recovery in a single system. With Scale Computing HC3, RAS administrators can provide faster VDI solutions at a more affordable price.
With Parallels RAS, It’s Easier to Be PCI DSS Compliant
Parallels RAS allows administrators to build a secure private cloud where they can centralize all sensitive data, allow access through published applications and virtual desktops, and have a PCI DSS-compliant network.
Since all data is centralized and only accessed via published resources, it is easy to manage, maintain, and audit the network. Because only published data is exchanged between the client and Parallels RAS servers, the security of the network is drastically improved.
The Parallels RAS Client is available for most popular operating systems and mobile devices. It’s also integrated with HTML5-enabled browsers, which makes it a client-independent solution. A unique and straightforward licensing plan offers both published applications and a VDI solution. Complete integration with the latest machine cloning technologies allows administrators to quickly deploy new machines to their environment or replace infected machines that may compromise network security.
Try Parallels RAS today and create a PCI-DSS compliant IT infrastructure!
References
Official PCI Security Standards Council Site – Verify PCI Compliance | https://www.pcisecuritystandards.org/pci_security/
PCI Compliance Guide Frequently Asked Questions | PCI DSS FAQs – https://www.pcicomplianceguide.org/faq
What is PCI DSS Compliance? – GlobalSign | https://www.globalsign.com/en/blog/what-is-pci-dss-compliance/

