
How to Authenticate Using Yubikey Smart Card in Parallels RAS
A smart card is a physical, electronic device commonly used to provide two-factor authentication when accessing a resource. The authentication process is based on two factors, the smart card itself and a password known by the user. Unlike Windows authentication, the user needs to know only the smart card’s personal identification number (PIN) to access a resource since the username is obtained automatically from the smart card.
Many companies choose the Yubico smart card over other manufacturers’ solutions due to its benefits, such as its enhanced security, easy set-up, and compatibility across multiple devices. Parallels® Client for Windows supports Yubico YubiKey use for Personal Identity Verification (PIV) for smart-card authentication.
This post covers a step-by-step guide for installing and configuring YubiKey smart-card authentication on Parallels® RAS.
Prerequisites Needed Before Installation
Before continuing with the steps described in the section below, please check that your environment meets these requirements:
- YubiKey Smart Card Minidriver for Windows is required for the certificate renewal process because the Windows built-in Minidriver cannot write to third-party smart cards. Note that the YubiKey Minidriver cannot be used simultaneously with the YubiKey Manager to provide Windows user credentials.
- Microsoft Windows Server 2012 R2 or later for servers.
- Microsoft Windows 8/8.1 or later for clients.
- Microsoft Windows Active Directory domain environment.
- Public key infrastructure (PKI) service.
- Parallels RAS 18.1 or later.
Install YubiKey Smart Card with Parallels RAS
- Ensure that each domain controller is issued a certificate. If a Microsoft Enterprise Certification Authority is already installed in your Active Directory, all domain controllers automatically enroll for a domain controller certificate. For third-party certification authorities, additional steps will be required.
- In the PKI solution deployed in your environment, generate the certificate template that will be used to create the authentication certificates. Please note that the certificate must meet the following criteria:
- The Key Usage field must contain a digital signature.
- The Subject Alternative Name (SAN) field must contain a User Principal Name (UPN).
- The Enhanced Key Usage field must contain smart-card logon and client authentication.
- To deploy authentication certificates to your users, choose one of the following alternatives for the certificate enrollment method:
- User self-enrollment: Clients will automatically request and load login certificates.
- Enrolling on behalf of other users: Accounts with elevated rights will enroll certificates on behalf of other users.
- Advanced enrollment: Use the YubiKey Manager command line.
- Install the YubiKey Minidriver on the client, the RAS Publishing Agents, and the destination session hosts.
- A valid certificate must be installed on a user’s device to use smart cards. To do so, you must import the certificate authority root certificate into all the device’s keystore. The root certificate will automatically be deployed if all your clients and servers are domain-joined and you use a Microsoft Enterprise Certification Authority.
- Once the end user receives the certificate generated by the certification authority, this certificate must be imported to the YubiKey Smart Card either by using the CertUtil tool or the YubiKey Manager.
Once you have configured and deployed the authentication certificates to the YubiKey and installed the YubiKey Minidriver in clients and session hosts, you need to enable smart-card authentication in Parallels RAS. Here’s how:
- Open the Parallels RAS Console, and click on the Connection category.
- Select the Authentication tab, and select the Smart Card option. In the Allowed authentication types section, select the Smart Card option.
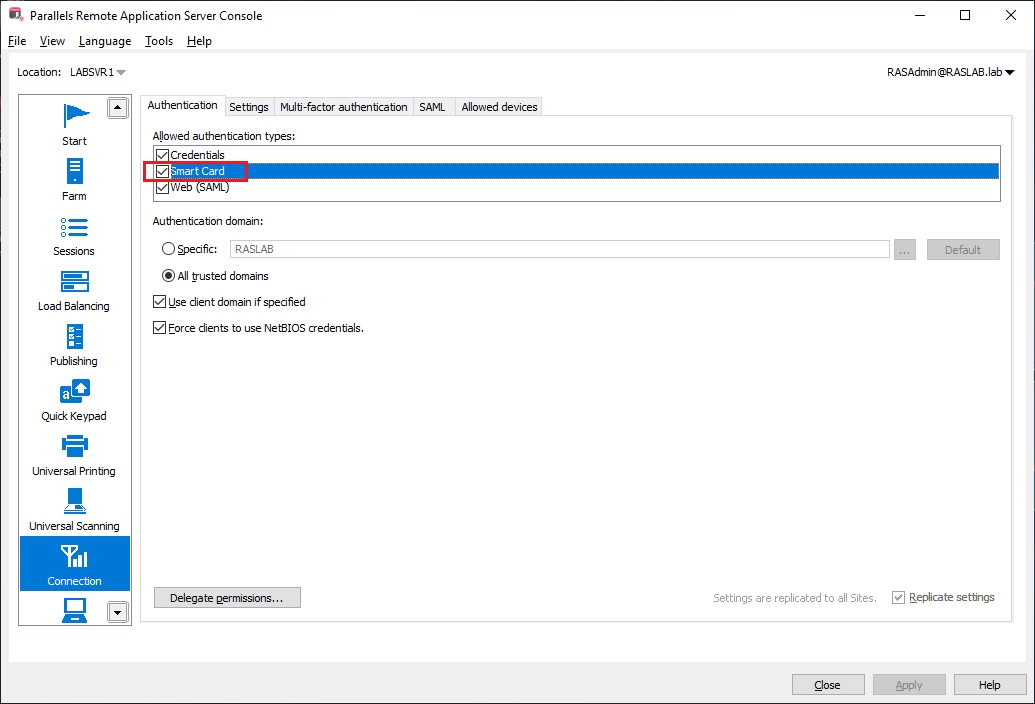
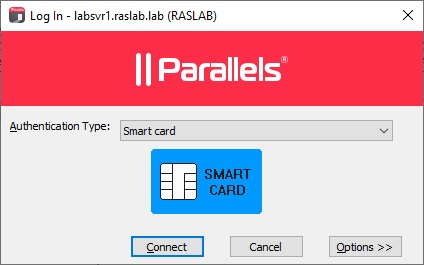
Your Parallels RAS setup is now ready to authenticate users using Smart Card. Users need to select Smart Card as the authentication type in their Parallels Client when logging in to the Parallels Client:
Secure Your Organization with Two-Factor Authentication and Parallels RAS
More and more companies have decided to introduce multi-factor validation mechanisms to strengthen the security of their users’ authentication processes.
Smart-card authentication is based on two factors, the smart card itself, where the username is stored, and a PIN known by the user. Therefore, to complete the authentication process, the user must possess the physical smart card and needs to know the smart card’s PIN.
Parallels RAS supports smart-card authentication, including supportability for Yubico YubiKey when used for Personal Identity Verification (PIV). The YubiKey 4 and 5 series and the YubiKey NEO support the PIV interface specified in the NIST SP 800-73 document “Cryptographic Algorithms and Key Sizes for PIV”.
In addition, Parallels RAS includes other different multi-factor authentication (MFA) alternatives for user authentication. The multi-factor authentication process is usually based on two successive steps—the first employs native authentication based on a combination of user and password. In contrast, the second step can be carried out in the form of Azure MFA (RADIUS), Duo (RADIUS), FortiAuthenticator (RADIUS), TekRADIUS, Deepnet, SafeNet, and Google Authenticator.
Check out how the built-in security features of Parallels RAS can help organizations comply with their security policies!

