
Perimeter Firewall: What Is It, and How Does It Work?
Over 30 years ago, the concept of a firewall entered the IT security conversation. Even today, the technology still plays a vital role in enterprise security, facilitating secure connectivity between different networks. As a mechanism of filtering out malicious traffic before it crosses from a public network into a private network, a perimeter firewall has ascertained its merit over the decades.
As with any persistent technology, it has obviously spawned many iterations. Discover how a perimeter firewall prevents network intrusions in this post.
What Is a Perimeter Firewall?
A perimeter firewall is a security application that defends the boundary between an organization’s private network from public networks such as the internet. You can implement a perimeter firewall as either software, hardware or both to act as the first line of defense in enterprise security. When implemented, a perimeter firewall inspects packets coming in and out of a private network and either allows or blocks them based on pre-determined rules.
These rules—defined in access control lists (ACLs)—specify what network names, internet protocol (IP) addresses, and port numbers are permitted. You can configure these rules to control inbound and outbound traffic as shown below:
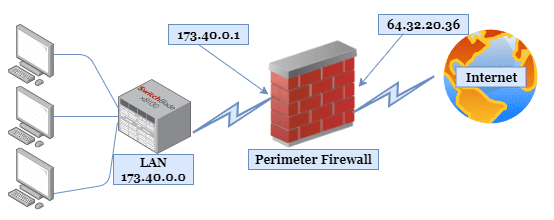
The primary goal of installing a perimeter firewall is to guard against external attacks. You can also install them within the organization’s network to create segmentation and thwart insider threats. Besides providing the first line of defense against attacks, perimeter firewalls can also record logging and audit events. Network administrators can use these records to identify user patterns and enhance rule sets.
What Is a Network Perimeter?
The terminologies network perimeter and firewall are sometimes used interchangeably, albeit with different meanings. A network perimeter is the edge of an organization’s internal network. It is the boundary between a company’s internal network and public networks such as the internet—or any uncontrolled external network.
A firewall, in contrast, is part of the network perimeter whose goal is to filter out malicious traffic before it crosses the boundary from a public network into an organization’s internal network. Besides a firewall, other components of a network perimeter include:
- Border routers. A border router is any router with a foot in two networks: one going to the public network and the other into the company’s internal network. A border router directs traffic into and out of the company’s internal network. It is the last router that network administrators can access and manage before traffic leaves the organization’s network.
- Intrusion detection systems (IDSs). An IDS is a passive monitoring component—implemented as either hardware or software—that monitors a network for suspicious activities, known threats or policy violations. An IDS automatically reports such activities by sending alerts when it discovers them.
- Intrusion prevention systems (IPSs). An IPS operates much like an IDS since it also monitors the network for malicious activities and policy violations. However, unlike the traditional IDS that is passive, an IPS can defend the target automatically without any network administrator intervention in case it discovers any malevolent activity or rule violations.
- Demilitarized zones (DMZs). A DMZ is any subnet that sits between the company’s internal network and public networks. It allows an organization to access untrusted public networks while ensuring the internal networks remain secure.
How Does a Perimeter Firewall Work?
As the primary defense line against attacks, perimeter firewalls employ different techniques to control traffic between an organization’s network and untrusted networks. Let’s discuss a few of them.
Static packet filtering
Static packet filtering is a technique where the firewall filters traffic based on packet fields and the network administrator’s rules. A static packet filter examines each packet it receives and compares it against ACLs. It then accepts or blocks the traffic into the organization’s network based on what the rule specifies.
Static packet filtering is among the oldest firewall techniques and operates at layers three and four of the open systems interconnection (OSI) model. As such, it cannot differentiate between the application layer protocols. It also cannot prevent spoofing attacks.
Proxy-based firewalls
A proxy-based firewall serves as a gateway between end users and the public network. Hosts connect to the proxy server, which makes a separate connection to the public network. Before transmitting packets to the public network, a proxy server can filter them to enforce network policies. It can also mask the end user’s IP address to protect it from the untrusted network.
Stateful packet inspection
Also called dynamic packet filtering, stateful packet inspection actively monitors the status of connections in a network. By maintaining the status of active connections, these firewalls can, for instance, waive monitoring on incoming traffic if the packet has already been inspected. This way, stateful packet inspectors prevent spoofing and enhance network performance.
Next-generation firewall (NGFW)
A typical NGFW leverages both static packet filtering and stateful inspection and has some features, including deep packet inspection (DPI), to achieve enterprise-wide security. It may also incorporate advanced security features such as network security systems (IDS and IPS), antivirus filtering and malware filtering to enhance security further.
What Are the Benefits of Using Firewalls?
Implementing firewalls can help an organization in the following ways:
- Monitor network traffic. Traffic coming in and going out of your network creates opportunities for threats that can compromise your operations. Monitoring and analyzing the network can help you keep your systems protected.
- Prevent hacking. Cybercriminals continue to unleash more complicated attacks and threats. According to the Center for Internet Security, external hackers were responsible for approximately 70% of breaches in 2020. With the steep climb in reported hackings, perimeter firewalls have become more important than ever in preventing external hackers from entering an organization’s network.
- Prevent virus attacks. Malicious developers create hundreds of thousands of new viruses each day, whose damage costs are immensely high to the organization. A perimeter firewall is beneficial because it can control your network’s entry points and prevent virus attacks.
- Prevent spyware. Ever since the world became data-driven, malicious individuals have programmed hundreds of thousands of spyware to access networks. Implementing a perimeter firewall is the first step towards blocking spyware.
- Promote privacy. No organization likes its data stolen, especially when it’s evident that it could have taken steps to prevent the intrusion. When you proactively work to ensure your customers’ data remain safe, you build an environment that clients can trust.
Enhance Data Security with Parallels RAS
Virtually all organizations have their IT infrastructures built on top of the transmission control protocol/internet protocol (TCP/IP) networking stack. Unfortunately, network designers conceived TCP/IP for openness and not security. Cybercriminals know that security vulnerabilities abound in any IT infrastructure.
While implementing a perimeter firewall can help you achieve enterprise security, it is not enough. It is only the first step in many strategies involving layered security that can help you achieve enterprise-grade security. Parallels® Remote Application Server (RAS) is one solution, incorporating a layered security approach that can robustly protect corporate resources.
As an all-in-one virtual desktop infrastructure (VDI) provider, Parallels RAS facilitates anywhere and anytime access to corporate resources from any device with data never leaving the datacenter. Besides centralized management of virtual desktops and applications, Parallels RAS also provides the following additional security features that can streamline perimeter firewalls:
- Multi-factor authentication (MFA). Users authenticate to Parallels RAS in two successive steps to access virtual applications and desktops. Parallels RAS also supports third-party authentication services such as RADIUS, Deepnet, Azure MFA, Dup and SafeNet.
- Data segregation. Users can create multiple independent sites inside the same Parallels RAS farm in a multi-tenancy environment.
- Advanced filtering. IT administrators can define various filtering rules such as usernames, IP addresses, or gateways that define how corporate resources get accessed.
- Security assertion mark-up language (SAML) single sign-on (SSO)authentication. Parallels RAS simplifies federated identity management via SAML SSO protocols such as Azure, Okta and Gemalto.
- Kiosk mode. IT administrators can transform endpoints running obsolete Windows versions, including Windows 7, 8 and 8.1, into a kiosk-like device without OS replacement.
- Smart card authentication. Users can leverage smart cards instead of usernames to access published corporate resources.
- Robust protocols. Parallels RAS uses foolproof protocols such as secure sockets layer (SSL) or federal information processing standards (FIPS) 140-2, and data compliance protocols like general data protection regulations (GDPR) to further enhance security.
Download your Parallels RAS trial today to achieve a foolproof perimeter firewall!

