
What Is VPN and What Are Its Alternatives?
Since the world and the global economy are now interconnected, many organizations have offices and facilities that span different geographical boundaries. And as the need for secure and reliable corporate data access becomes necessary, companies turn to virtual private networks (VPNs).
By creating a secure and encrypted connection over a public network infrastructure, a VPN can facilitate remote access to corporate files and applications. Learn more about what a VPN is, how it works, its benefits and limitations, and its alternatives in this post.
Definition of a Virtual Private Network (VPN)
As the name suggests, a VPN is a private network that uses the internet to connect to a remote site. Rather than using a dedicated, point-to-point, or leased line, a VPN uses an encrypted “virtual” connection over the internet to create a secure connection to a remote site. VPNs have been in existence since 1996 when a Microsoft employee implemented a peer-to-peer tunneling protocol (PPTP).
This protocol created a private and secure connection between users by encrypting data and tunneling it over a local area network (LAN) and a wide area network (WAN). All you needed to send data via PPTP securely was your credentials (username, password and the server’s internet protocol (IP) address).
At the time, VPNs primarily facilitated remote access to corporate applications and files for mobile users and employees in branch offices. In the early 2000s, other VPN use cases emerged as the internet’s popularity grew, and users began to worry about privacy and security.
Today, you can use a VPN to:
- Browse websites securely and privately.
- Overcome censorships and restricted-access sites.
- Gain some level of anonymity online by concealing your true location.
- Bypass restrictions are placed on some websites in certain geographical locations.
Functionality of VPNs
At its most basic level, a VPN connects your device (laptop, tablet, or smartphone) via software to another computer (the VPN server). You need a reliable VPN provider and must download and install its software (also called a VPN client) to your device. After installing the software, you must configure your preferred security settings, including your credentials and the VPN protocol, to get started.
How Do VPNs Work?
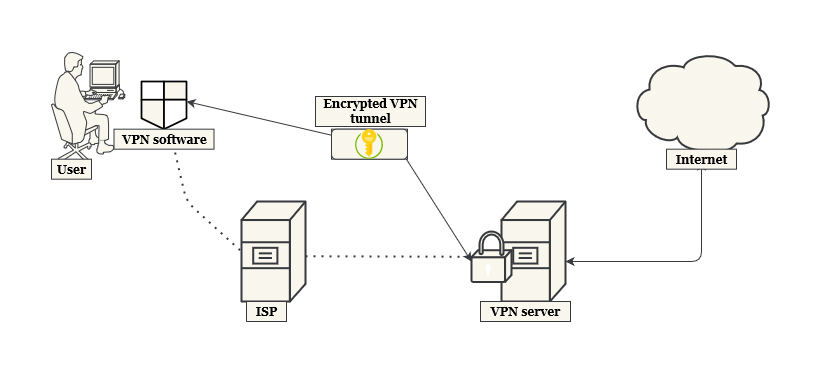
When you establish a secure connection via VPN, here’s what happens:
- The VPN software encrypts the data on your device and transmits it to a VPN server via a secure connection.
- The VPN server decrypts data from your device.
- The VPN server creates a point-to-point connection over the internet and transmits your data to the remote server, which replies.
- The VPN server encrypts the traffic from the remote server and transmits it back to you.
- The VPN software on your device decrypts the data so you can decipher and use it.
Benefits of VPNs
There are three key benefits that VPNs provide to organizations:
Remote access
Organizations can leverage VPNs to increase productivity. Employees don’t have to get tied to one particular location as they work—they can work from anywhere and anytime by accessing corporate files and applications securely via a virtual private network.
Security
Organizations can also use VPNs to enhance security. By encrypting data in transit, a VPN secures your connection to the remote server.
Privacy
A VPN masks many things about your connection, such as location, IP address, and search history. This prevents your connection from being tracked by governments, cable companies, and ISPs.
But that’s not all. A VPN may also offer the following benefits:
- Accessing geo-blocked websites. A VPN replaces your real IP address with that of the VPN server you’ve connected to. So, any site you connect to via a VPN sees only the IP address of the VPN server and not yours.
- Bypassing internet censorship. By creating an encrypted tunnel between the local PC and the VPN server, a VPN can bypass internet service provider (ISP) rules that block and filter certain IP addresses. This means any internet activity gets routed via the VPN and cannot get traced back to you.
- Downloading files faster. If your ISP often throttles download applications such as BitTorrent, you can use a VPN to bypass the rules to get faster download speeds.
Limitations of VPNs
While a VPN might seem like a perfect solution to surfing problems because of enhanced privacy and security, it has some limitations, including:
Reliance on client hardware and connection speed
VPN connections are bound to the users’ hardware. Users must install a VPN client on their endpoints to access remote resources such as shared folders, Universal Naming Convention (UNC) paths, or virtual machines. This can get complicated for IT administration that needs to support multiple devices, especially in a bring-your-own-device (BYOD) environment. Virtual desktop infrastructure (VDI) technologies can leverage web interfaces that are device-agnostic without the need to install software on user devices.
Require suitable end-user hardware
VPNs shift the processing work to the clients. If PCs are too old to run the organization’s applications, then you have to purchase new ones for them. Getting a brand-new PC up and running with all the organization’s applications can be difficult and expensive. You must work out how the applications on the employees’ machines get installed and updated. Since your employees are remote, maintaining their off-site resources is tricky.
Not foolproof
Most VPNs conduct security checks, like ensuring that the endpoint is up to date with the latest patches and antivirus pattern files. In some instances, you can have many endpoints establishing a connection to the VPN server. Under these circumstances, you may be compelled to lower your security safeguards to allow many machines to connect to the server. Additionally, data that your employees work with may be copied locally to their devices. This can compromise the company’s data and put you at risk. IT administrators must take extra steps to protect the organization’s data.
An Alternative to a VPN Is Virtual Desktop Infrastructure (VDI)
Until the early 2000s, VPNs were among the most popular go-to technologies for secure access to corporate data and applications. But times have changed. Increasingly, more organizations are migrating their workloads from on-premises datacenters to the cloud. Under cloud-first environments, you must rethink your strategy if you’re still leveraging VPNs for remote access.
While most VPNs enforce some form of security health checks before endpoints can connect to enterprise networks, there are no guarantees that remote endpoints will adhere to them. Also, the process of configuring such devices to conform to the security policy may be tedious and laborious for IT administrators.
Plus, data and applications still reside on the endpoints. If such devices get lost or stolen, an organization can get compromised. A virtual desktop infrastructure (VDI) is another alternative to a VPN since it can facilitate remote access from any device and platform while keeping corporate assets secure.
With VDI, employees can access their corporate files and applications securely so long as they have an internet connection. A VDI solution is more secure than a VPN because it centralizes IT resources management, so IT administrators have full visibility of all the corporate assets. And since data and applications get stored on a centralized server rather than on the endpoints, VDI is foolproof.
Additionally, you don’t need suitable hardware to use VDI since it shifts processing from the client endpoint to a centralized server. Employees can use any device, including machines that have reached end-of-life, thin clients, and smartphones, to access their virtual workspaces.
Parallels RAS Is an All-in-One VDI Solution
If you’re thinking of implementing a low-cost, simple-to-set-up, and secure solution for remote access, perhaps it’s time you considered Parallels® Remote Application Server (RAS). As a leading VDI provider, Parallels RAS incorporates the greater benefits of desktop virtualization.
Parallels RAS is an all-in-one VDI solution that you can leverage to allow employees to access corporate desktops, files and applications securely from anywhere, at any time, and on any device—including any HTML5-ready browser. As a VDI provider, Parallels RAS centralizes and streamlines the management of entire IT infrastructures and multi-cloud deployments while enhancing data security.
Try out all the Parallels RAS benefits for yourself by downloading your free 30-day trial today!

