For thrill-seekers and adrenaline enthusiasts alike, Rocket League is the ultimate outlet.
This game combines the exhilaration of high-speed car action with the strategic depth of soccer, captivating players with its dynamic...
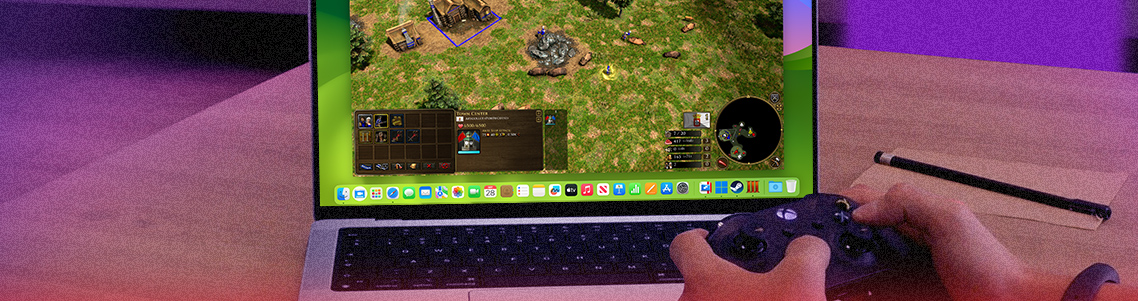
In a world where strategy is paramount and maintaining your dominion requires both strength and wisdom, the Age of Empires games have long captivated players with their immersive universe of historical grandeur and...
Virtualization technology allows us to create multiple virtual machines (VMs) on the same physical machine.
A virtual machine operates like a software program running on a...
Over the years, I’ve closely watched Apple’s strides towards enhancing user privacy and security.
The recent release of Apple’s PQ3...
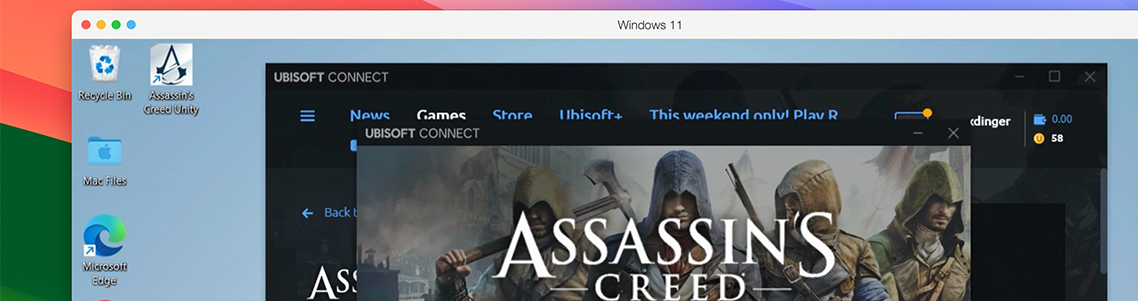
Embarking on the rich, layered odysseys in the Assassin’s Creed realm is akin to a rousing call to arms for the historical adventurer within us.
Yet, Apple...
Hello, Parallels Desktop fans! Our unstoppable engineering team continues to innovate, moving the needle further. I am happy to share another significant milestone for Parallels Desktop 19 for Mac and introduce you to our third...
In the boundless world of digital gaming, where whispers of adventure beckon the brave and the bold, there exists a realm where even the most treacherous quests can be undertaken from the sanctuary of...
In the ever-evolving landscape of university IT, optimizing resources and ensuring seamless operations is paramount. Parallels Desktop stands out as a powerful tool for bridging the gap...
Software developers have traditionally had to rely on a single workstation to develop, simulate production, and run tests for all their projects.
However, with the rise of virtual machines (VMs),...
As a student, navigating through various courses often means dealing with a multitude of software requirements.
The challenge intensifies...