Why do organizations user browser isolation instead of VPNs?
Remote Browser Isolation (RBI) secures web browsing by isolating activity from a user’s device and network, protecting against web-based threats. Essentially, browser isolation is an alternative to a VPN.
Virtual Private Networks (VPNs), on the other hand, encrypt data and hide IP addresses to secure all internet traffic.
Key Features to Look for in a VPN Provider
1. Ease of setup and maintenance
RBI solutions, especially cloud-based ones, are easier to set up and maintain compared to VPNs.
They require minimal user configuration and include automatic updates.
VPNs involve more extensive setup, frequent updates, and ongoing management.
2. User access controls
RBI allows IT admins to block malicious or non-work-related websites, offering better access control.
VPNs, while securing access to organizational systems, lack these controls.
3. Functional differences
RBI protects against web-based threats by isolating user browsing in a sandbox, preventing malware and phishing attacks.
VPNs, on the other hand, secure internet traffic by encrypting data and masking IP addresses, making them ideal for privacy and protecting data in transit.
4. Support for Zero Trust
RBI aligns with zero trust principles, treating all web sessions as potentially dangerous and isolating them to block threats like ransomware.
VPNs implicitly trust devices or users once connected, which can lead to broader access to internal resources.
5. Malware protection
RBI protects against malware by remotely executing and rendering web sessions, ensuring malicious content cannot affect users’ devices or networks.
VPNs provide no such protection against malicious URLs or files.
6. Browser vulnerability protection
RBI neutralizes browser vulnerabilities, including zero-day threats, by executing content remotely in a safe environment.
VPNs do not offer this level of browser protection.
7. Scalability
RBI solutions, especially cloud-based ones, scale easily with user growth without requiring significant additional resources.
VPNs are less scalable, often needing extra hardware or cloud resources.
8. End user experience
RBI is user-friendly, with seamless interaction and minimal training required.
VPNs demand more effort from users, such as manual connection, credential entry, and navigating latency issues.
Why do I need a VPN?
Whether for security, privacy, or unrestricted access, a VPN is a valuable tool for safer and more open internet usage.
A VPN helps organizations keep their data safe by encrypting the internet connection, allowing them to share files securely without exposing sensitive information.
It is especially useful when using unsecured networks such as public Wi-Fi. In this case, a VPN keeps hackers away from your data and information.
VPNs help users maintain privacy by IP address masking, preventing websites, advertisers, and even your internet service provider from tracking your online activity.
A VPN also allows you to access restricted content that may be limited to specific regions.
How VPNs Protect Your Data and Network
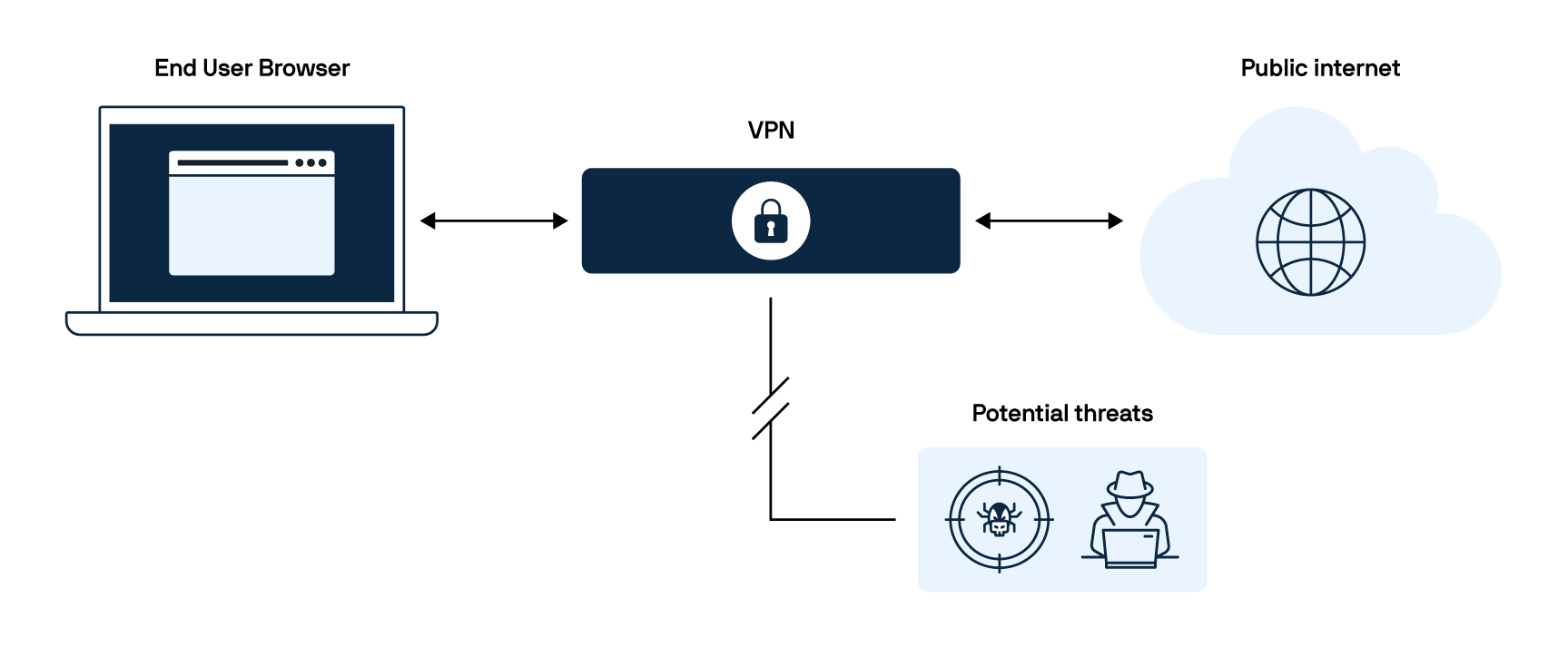
A VPN creates an encrypted and secure connection between your device and the internet.
When you connect to it, your internet traffic is routed through a remote server, similar to a tunnel, which masks your IP address and makes it appear like you are browsing from a different location.
This encryption protects your data from hackers, internet service providers, and other third parties trying to monitor your activity.
What attacks can VPNs protect against?
Although a VPN alone won't shield you from all cyber threats, it can make a big difference when it comes to these specific types of attacks:
Distributed Denial-of-Service (DDoS) attacks
A DDoS attack usually entails flooding a network, server, or website with overwhelming traffic, resulting in slowdowns or complete outages of the targeted networks.
As a VPN hides your IP address, it complicates pinpointing and targeting your network.
Man-in-the-Middle (MitM) attacks
When you are connected to unsecured public Wi-Fi, such as those found at cafes, airports, or hotels, you can be the victim of a MitM attack.
A MitM attack occurs when an attacker intercepts communication between two parties: you and the site you are using.
Through this attack, hackers can get access to your login credentials, payment details, or sensitive messages without your knowledge.
As a VPN encrypts your internet traffic, all of this information becomes unreadable to anyone trying to peak at your connection, making it unusable for hackers.
Packet sniffing
Cybercriminals use packet sniffing tools to capture unencrypted data sent over networks.
This method can expose sensitive details like passwords, emails, and financial transactions, especially when using unsecured Wi-Fi.
A VPN ensures that all encrypted data leaving your device remains unreadable, even if someone intercepts your network traffic.
This encryption protects your personal and business communications from prying eyes.
Malware infections
Some VPNs offer features like ad and tracker blocking, phishing protection, and access to safer DNS servers, reducing the risk of exposure to malicious sites.
Session hijacking
When you log into an online platform, a session ID is created to keep you logged in for easy access.
While convenient, hackers could intercept it.
A VPN encrypts your online activity, making it much harder for anyone to steal your session ID.
Digital footprint leaks
Digital footprints are the traces, such as cookies, browsing history, and IP addresses, you leave behind when using the internet.
Details and information like these can be used to track you, and hackers can use them for personalized cyber attacks.
Because a VPN encrypts your online activity, it also minimizes the risk of exposing your digital footprint.
What are the benefits of using a VPN?
VPNs do more than unblock content—they secure data, protect privacy, and enable safe remote work.
Accessing geo-blocked websites
When most people think of VPNs, they often associate them with streaming shows or movies from different countries.
In a business context, however, VPNs can be valuable for accessing region-restricted corporate resources, research materials, or cloud services that may not be available in certain locations.
Use public unsecured Wi-Fi safely
Hackers frequently target public Wi-Fi networks due to their inherent security vulnerabilities.
These networks are often unsecured and lack encryption, which makes it easy for attackers to intercept data, steal credentials, or execute man-in-the-middle attacks.
However, using a VPN can significantly reduce these risks, as it encrypts your activity and location.
Enabling safe remote and hybrid workforces
Remote and hybrid workforces work from many different devices, locations, and networks.
With a VPN, everyone can safely log on from wherever they are without compromising the organization's data or sensitive information, enabling secure file sharing across different locations.
At the same time, they can also access all resources even if they are located in a different area than where the content is restricted.
Hides private information and sensitive data
A VPN encrypts your internet traffic, making it nearly impossible for hackers, advertisers, or even your internet provider to track your online activity.
This added layer of security ensures that sensitive data—such as passwords, banking details, and personal messages—remains private, even when using public Wi-Fi.
Avoid Internet Service Providers (ISP) throttling
Internet Service Providers sometimes slow down your connection based on your online activities, especially when streaming, gaming, or downloading large files.
This slowdown is known as throttling, and it can make your internet experience frustratingly slow.
A VPN helps you avoid throttling by encrypting your traffic, preventing your ISP from seeing what you're doing online.
Without this visibility, your ISP can't selectively slow down your connection, allowing you to enjoy faster and more consistent speeds.
Here are 7 alternatives to VPNs
When it comes to keeping your organization safe, there isn't one right answer for everyone. While VPNs are a popular way of doing so, there are other alternatives to consider, depending on your needs.
Zero Trust Network Access (ZTNA)
Unlike a VPN, which grants broad access to a network once a user is authenticated, ZTNA follows a “never trust, always verify” model.
Every request is authenticated before granting access to specific applications, reducing the risk of attackers moving laterally within a network.
This makes ZTNA a more granular and secure alternative to VPNs, especially for businesses handling sensitive data.
Best for: Secure remote work and least-privilege access.
Remote Browser Isolation (RBI)
A VPN encrypts all traffic, but it still allows users to interact directly with potentially dangerous websites.
RBI solutions like Parallels Browser Isolation eliminate this risk by isolating web sessions in a secure cloud environment.
Instead of sending website data to the user's device, RBI streams only a safe, interactive image of the site, blocking malware, phishing, and browser-based exploits.
Best for: Safe browsing with VPN slowdowns.
Secure Access Service Edge (SASE)
Larger organizations with remote workers can face efficiency issues with VPNs as they route all traffic through centralized servers, which can create bottlenecks.
SASE replaces VPNs by integrating networking and security into a cloud-based service, delivering secure, direct access to applications without requiring users to connect to a traditional corporate network.
Best for: Large organizations with remote teams.
Identity and Access Management (IAM) and Privileged Access Management (PAM)
VPNs authenticate users at the network level, meaning once inside, they often have access to a broad range of resources.
IAM and PAM provide a more controlled alternative by verifying user identities and enforcing strict access policies for individual applications or sensitive data.
IAM ensures that only authorized users can log into applications, while PAM adds extra protection for high-privilege accounts.
Unlike a VPN, these solutions don't give users access to an entire network—only to what they're explicitly authorized for.
Best for: Identity-based security instead of full-network access.
Virtual Desktop Infrastructure (VDI) or Desktop-as-a-Service (DaaS)
VPNs allow remote employees to access company resources but also expose the network to potential risks if a device is compromised.
VDI and DaaS solutions provide a more secure alternative by hosting the entire work environment in the cloud or a data center.
Employees connect to a virtual desktop rather than directly accessing corporate resources, reducing the attack surface.
Best for: Secure, centralized remote work solutions.
Proxy servers
A proxy server functions similarly to a VPN in that it hides your IP address, but it doesn't encrypt traffic like a VPN does.
That makes proxies useful for bypassing geo-restrictions or basic anonymity but not for security-sensitive activities.
Unlike a VPN, which encrypts all traffic, a proxy only reroutes specific web requests.
While not a direct security alternative, proxies are a lightweight option for those who just need privacy without the overhead of a VPN.
Best for: Bypassing geo-restrictions, lightweight privacy.
SSH tunnel
SSH tunneling allows users to securely connect to remote systems without using a VPN.
Instead of encrypting all internet traffic like a VPN, SSH tunnels encrypt only specific connections, such as accessing a private company server.
That makes SSH a lightweight, flexible alternative for secure remote access without the need to connect to a full VPN.
Best for: Secure access to internal company systems.
See how Parallels Browser Isolation can be a powerful VPN alternative
VPN Use Cases for Work and Personal Security
VPNs are commonly used to secure internet connections, protect privacy, and access restricted content. But VPNs aren't the only solution.
Alternatives like browser isolation, ZTNA, and SASE offer better security and performance in some cases.
1. Secure remote work
VPNs encrypt internet traffic, allowing employees to access company resources safely from anywhere. If compromised, VPNs can expose entire networks.
Alternatives like ZTNA ensure that users access only the applications they need, thereby reducing security risks.
2. Protecting data on public Wi-Fi
Public Wi-Fi networks are easy targets for cyberattacks, but VPNs encrypt data to keep it secure from hackers.
However, remote browser isolation offers a safer alternative by keeping all web activity in a secure, cloud-based environment—preventing malware and phishing threats.
3. Bypassing geo-restrictions
VPNs can help access content restricted by region by masking a user's IP address. Proxy servers can also perform a similar function without requiring full traffic encryption.
4. Avoiding ISP throttling
Some internet service providers deliberately slow down specific types of traffic, such as streaming and gaming. VPNs can help by concealing online activity from ISPs.
3 examples from organizations using Parallels solutions as a VPN alternative
VPNs have long been the go-to solution for remote access, but they come with limitations: performance bottlenecks, high costs, and complex management.
As businesses shift toward more flexible and secure remote work solutions, many are replacing VPNs with alternatives that provide smooth access without the headaches.
Take Fondazione Telethon, for example. They saved 70% in IT operations after replacing its costly and inefficient VPN-based remote access with Parallels RAS.
By making the switch, they eliminated performance bottlenecks and ensured smooth access to critical legacy ERP applications.
Similarly, Ajuntament de Malgrat de Mar transitioned from a traditional VPN-based setup to Parallels Secure Workspace, eliminating VPN dependencies entirely.
This shift strengthened security, improved flexibility, and reduced IT overhead, allowing employees to work efficiently from anywhere.
Managing IT infrastructure shouldn’t be a maze of complexities and high costs.
By switching from Citrix to Parallels RAS, XenTegra ONE simplifies remote access for its clients, cutting costs and eliminating unnecessary licensing headaches.
With a single console for administration, businesses can now securely access applications across on-prem, hybrid, and multi-cloud environments—without relying on a VPN.
Parallels Browser Isolation as a VPN alternative
Parallels Browser Isolation (PBI) is a secure alternative to VPNs, keeping web activity contained in a cloud-based environment.
Instead of routing all traffic through a VPN, PBI prevents malware, phishing, and data leaks by isolating browsing sessions—ensuring no harmful content ever reaches the local device.
Combined with solutions like Parallels RAS for secure remote access, the Parallels platform provides a more flexible, scalable, and performance-friendly approach to cybersecurity.
Resources
Learn more about why ZTNA solutions are forecasted to replace VPNs
The evolution of cyber threats: Actionable tips from the last three-year review
A single compromised VPN password was all it took to bring down critical infrastructure—discover how to prevent the same mistake in this whitepaper
The future of zero trust security: Recent trends and forecasts
Read more about why 60% of organizations are phasing out their traditional VPNs and switching to ZTNA
Take the next step with Parallels Browser Isolation
Explore the Parallels ecosystem and strengthen your security with Parallels Browser Isolation—your first line of defense against web-based threats. Discover how our solutions work together to keep your organization protected. virtual desktop infrastructure for organizations seeking to expand their virtualization capabilities, improve remote access to virtual apps and desktops, and streamline their IT process.







