What does phishing do? How does phishing work?
As a subtype of social engineering, phishing plays off of a user's established trust in a brand. It disguises bad URLs within an email that seems trustworthy—but when the user clicks, they don't go to the site they're expecting.
Protecting devices properly can defend users from these bad actors, even when they click on a link they shouldn’t have.
Phishing methods often involve:
Deceptive emails or text messages
Phishing emails or text messages are designed to trick users into trusting them. These messages look like they come from a trusted source, asking users to take an action they would expect that source to request.
Phishing text messages are also sometimes known as smishing messages, a combination of SMS and phishing.
Urgency to act
If users have time to double-check a phishing email, they may realize what it is—and an attacker doesn't want that.
Phishing scams will pressure users to act fast against their better judgment with tight deadlines or urgent requests.
This may be an account that needs updating before the user can access it, a payment that didn't go through, or even a claim that a password has been compromised.
Social engineering
Phishing relies on social engineering tactics to work.
Social engineering involves using human interaction for data theft.
Hackers may pretend to be new employees or representatives of a trusted charity, for example, to trick unsuspecting users into giving them access.
Malicious links or hidden URLs
Phishing messages will include links to malicious websites, often disguised as legitimate ones.
These sites likely contain malware and will attempt to infiltrate the user's device or network.
Fake login pages
A phishing message sometimes leads users to a fake login page designed to mimic a legitimate one.
When users add their login details like usernames and passwords, this information goes straight to the attacker.
Impersonation
Phishing attackers may pose as trusted colleagues or acquaintances to manipulate users' trust.
Organizations may see attacks like emails seemingly coming from an executive or client.
Domain spoofing
When targeting organizations, attackers may try to make phishing emails look like they're coming from the organization's domain so messages have a better chance of reaching potential victims.
Multi-channel phishing methods
More sophisticated phishing attacks will use multiple channels together to lure in users.
These attacks will target users through combinations of emails, text messages, social media, or even voice and video calls using AI or voice changers.
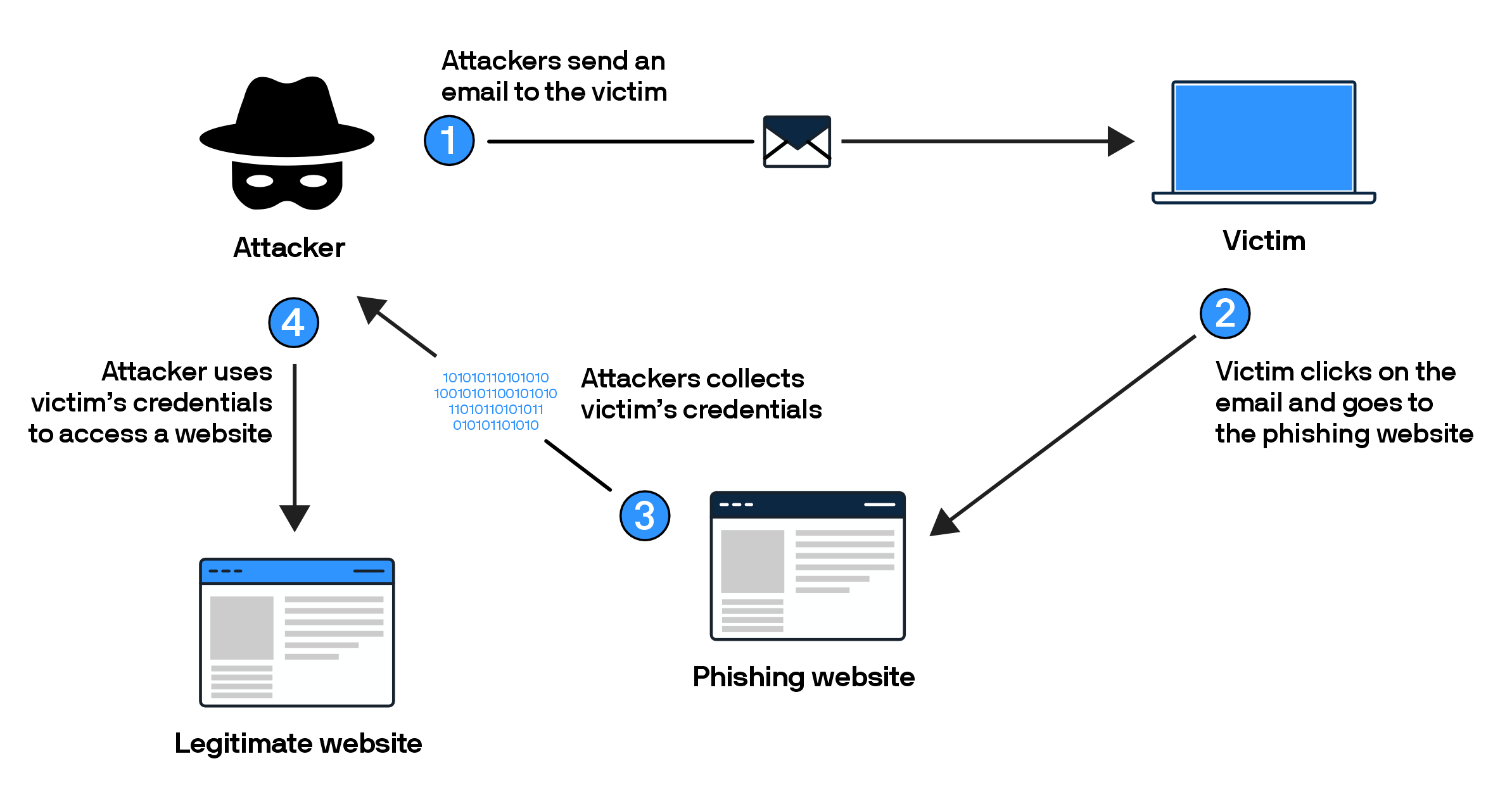
What are the goals of a phishing attack?
A phishing attack's primary goal is to trick users into giving a cybercriminal access to something valuable.
This could be usernames and passwords, financial details like credit card or bank account numbers, or sensitive business data.
It often works through a fake login page stealing login credentials, a fake purchase page stealing credit card information, or a malicious site that plants another type of malware onto the user's device or network.
Attackers will then use this information for other cybercrimes or data exfiltration.
Who or what are the targets of a phishing attack?
Phishing attacks can target both individuals and organizations.
- Attacks that target individuals are looking to gain login information or financial details from the individual for theft or identity fraud.
- Attacks that target organizations will go after individuals who are part of the organization, often employees or executives, to gain login information or sensitive corporate data.
There are a few specific tactics associated with these targets.
Spear phishing
Spear phishing is the practice of targeting individuals by gathering personally identifiable information to make the phishing attempt more convincing.
Whaling
Whaling is the practice of specifically going after high-value targets, including executives and members of the C-suite, in an attempt to access sensitive information.
What do I do if I suspect a phishing attack?
If you suspect you've received a message that may be a phishing attack, report it to your IT administrator. Don't click or respond in any way.
If you suspect you've been phished:
- Make a note of any information that you may have shared, like usernames, passwords, or account data.
- Notify your IT administrator.
- Change your passwords on affected accounts and anywhere you've used the same password.
- Check that you have multifactor authentication turned on, or set it up if you haven't already.
- Contact any outside parties you may need to alert, like banks or law enforcement, if financial information was taken.
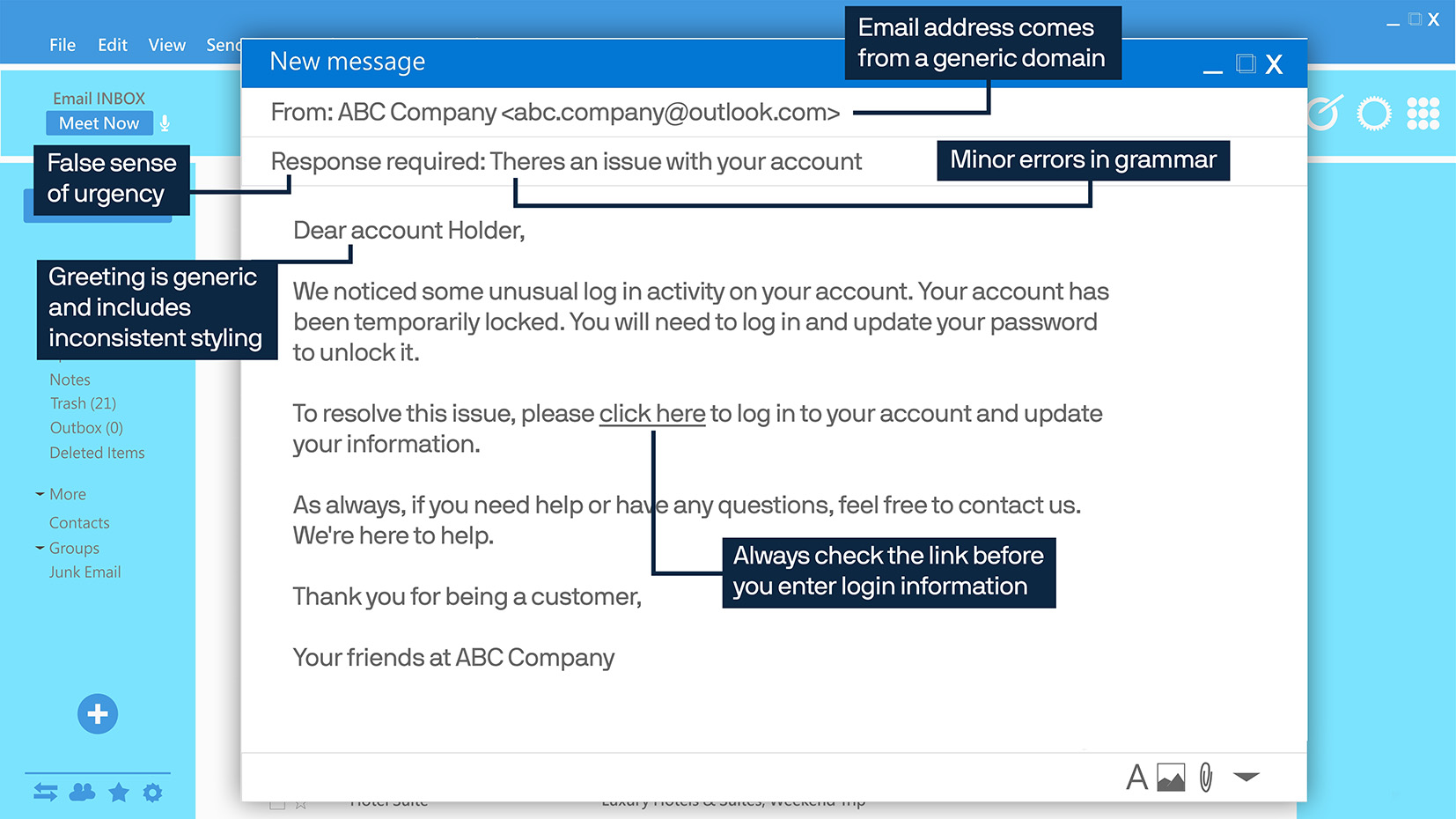
What does a phishing attack look like?
Phishing tactics will do their best to mimic a trusted source, going so far as to use a company's logo and brand styling—but there will be some signs that a message isn't legitimate.
To determine if a message you aren't sure about is suspicious, consider these questions:
- Does it mention an issue with your account or payment?
- Does it ask you to confirm personal or financial information?
- Does it want you to click on a link to confirm a payment or invoice?
- Does it mention a coupon or a government refund you weren't expecting?
You may also notice a few key traits about the email itself:
- Does the sender's email address look strange or generic?
- Does the subject line or greeting look too generic?
- Are there minor errors throughout the message?
- When you hover over a link, does it look different from what you'd expect?
Let's look at an example.
5 ways organizations can stay protected from phishing attacks
Phishing attacks can create major problems for an organization, and it's not always easy to see them coming.
With solid defenses in place, organizations can protect against the dangers of one deceptive email or bad link.
1. Zero Trust network access
Zero Trust access uses the philosophy that you should never trust, but always verify an unfamiliar source or device.
With this approach, organizations and individuals can protect themselves by verifying any device, user, network, or message before anything else.
2. Remote browser isolation (RBI)
Remote browsing isolation protects against phishing attacks by isolating a user's browser in a cloud-based environment, away from the device.
This way, even if the user clicks on a bad link, any malware lying in wait can't reach the device or network.
3. Employee education and awareness training
When employees know the risks and what they're looking for, they can take steps to protect themselves.
This training also gives them the knowledge to alert IT admins if they notice attacks.
4. Multifactor authentication (MFA)
Multifactor authentication gives individuals and organizations an extra layer of security by requiring a login code after the user inputs their credentials.
Even if passwords are compromised, a cybercriminal cannot get into the account without the MFA token.
5. Secure email gateways (SEGs)
Secure email gateways look for and block phishing attacks and malicious emails before they reach users' devices.
See how Parallels Browser Isolation can help your organization guard against phishing attacks.
Resources
Zero Trust and secure web access: The definitive cybersecurity implementation guide
Explore practical steps to protect your organization from modern cyber threats brought on by SaaS adoption and remote work—using Zero Trust principles and powerful tools like Parallels Browser Isolation.
Announcing our new secure web access solution, Parallels Browser Isolation
As organizations embrace remote work and cloud-first solutions, traditional security falls behind. Parallels Browser Isolation offers a cloud-based way to stream web content securely and give IT control—learn how it’s reshaping modern protection.
The evolution of Zero Trust in 2024 and beyond
Once a niche concept, Zero Trust has become a business-critical strategy. This whitepaper traces how it got there, where it's headed, and why it matters more than ever.
Take the next step
Parallels solutions protect your organization with a range of cybersecurity software that works together to fit your unique needs.
With its Zero Trust approach to core security, including secure browsing, control over policies, and monitoring and tracking functions, Parallels Browser Isolation helps organizations like yours stay safe from cyber threats like phishing.







